Azure Governance — The Importance of Role-Based Access Control (RBAC)
In our last article, we discussed the need for governance across your Azure cloud, including the best practices to govern cloud consumption and bills. But, cloud governance is not limited to just monitoring and controlling cloud costs. Role-based access control (RBAC) is an important element in the “Azure Governance” piece.
Access management for resources in Azure is a critical operation for any cloud-first or cloud-native business to ensure that its environment is compliant with external regulations and policies.
This article will give you a detailed overview of role-based access control (RBAC) and its essentiality in the Azure governance process, including a navigated approach to enforcing RBAC across your cloud ecosystem.
What is Azure role-based access control (RBAC)?
Azure role-based access control is a security approach that enables you to control:
● System access for users based on their roles defined within and across the organization
● Who are authorized to access Azure resources
● How they can access and what they can do with those resources, and
● What particular areas they are permitted to access
Azure RBAC is an access control and authorization system designed on top of Azure Resource Manager that allows you to manage the accessibility of Azure resources at a granular level.
Understanding key components of Azure RBAC
In Azure RBAC, you have to assign Azure roles to specific users as it works on the concept of enforcing a set of permissions for accessing cloud resources. You need to create a role assignment that comprises three key components – security principal, role definition, and scope to control resource access.
1. Security Principal
A security principal is an element in Azure RBAC that defines/depicts a user, group, service principal, and/or managed identity requesting access to resources. You can permit access to specific resources by assigning a role to any of these security principals.

2. Role Definition
Role definition is another key object in Azure RBAC that is a collective set of permissions and is generally just known by the term “role.” It incorporates a list of actions that can be performed by a user, such as read, write, or delete. A role can be a high-level, for example, an owner; or it can be specific such as a security reader.

3. Scope
The “scope” specifies or defines a set of resources that the role-based access applies to. You can define a scope to limit and restrict the actions allowed to a user when assigning a role.
For example, if you want to make a user the Virtual Machine Contributor, but only for one resource group, you can specify a scope at a hierarchical level. Azure usually allows you to define scope at the following levels:
- Management Group
- Subscription
- Resource Group
- Resource
The levels are listed in a top-to-bottom hierarchy as they are organized or structured in a parent-child relationship.
Why is RBAC important?
Role-based access control not only provides an added layer of security for your Azure environments but also allows the cloud users to do their jobs based on their assigned roles.
Using Azure RBAC, you can do the following to strengthen your governance and security control:
- allow a cloud user to manage all the resources included in a resource group, such as web apps, virtual machines (VMs), databases, storage accounts, subnets, etc.
- enable one user to manage VMs in a subscription and allow another user to govern virtual networks
- provide an application the access to all the resources organized in a resource group
- permit a Database Administrator (DBA) group to manage the SQL databases in an Azure subscription
Moreover, RBAC allows you to have better control over governance policies and improves your organization’s overall compliance posture. Enterprises, irrespective of their business type or nature, have to adhere to a set of regulations, compliance certifications, and confidentiality policies to manage their as well as customer data. Attaining compliance is a measure of commitment toward your customers and partners that ensures the security of third-party data, including your ability to safeguard sensitive data overall.
RBAC provides a consolidated structure to manage, monitor, and restrict access at an enterprise level. Implementing role-based access control in Azure helps administrators control who accesses a system and when, including what can be accessed by a particular individual and the type of authorizations they have to make any changes to the system, application, etc.
It not only enables you to resolve compliance issues but also simplifies the workflows for achieving regulatory requirements based on confidentiality, privacy, and security standards.
How does RBAC impact your Azure cloud security?
With benefits comes the concern for security in cloud, which is one of the most crucial and inevitable aspects of your entire governance strategy. You surely don’t want everyone inside or outside your organization to access sensitive cloud data, resources, etc. That’s when Azure policy and Azure RBAC help you manage your resources effectively and ensure security at a user level.
Incorporating RBAC adds an extra layer to your existing cloud security and safeguards the ecosystem in the following ways:
- Limits or denies the user access to the mandated levels required to complete a job
- Helps cloud-first businesses enforce security controls and best practices to prevent data leakage or breaches
- Strengthens security with the “Separation of Duty” (SOD) principle that allows no user access to enough control over resources to misuse or damage them
- If a breach occurs, RBAC restricts and minimizes the impact by limiting access to sensitive information for the role the attacker used as an entry point
Implementing governance across your Azure cloud
However, in addition to enforcing Azure RBAC for secured access to your cloud resources, you need to create compliant Azure environments by implementing a robust governance framework that empowers you with advanced monitoring capabilities.
According to Forrester’s report, The Forrester Tech Tide: Cloud Governance And Enablement Technologies, Q4 2020,
“By using a single tool to monitor 80% to 90% of IT services, I&O professionals can diagnose problems faster and, in some instances, identify issues and remediate them before service disruptions affect customers.”
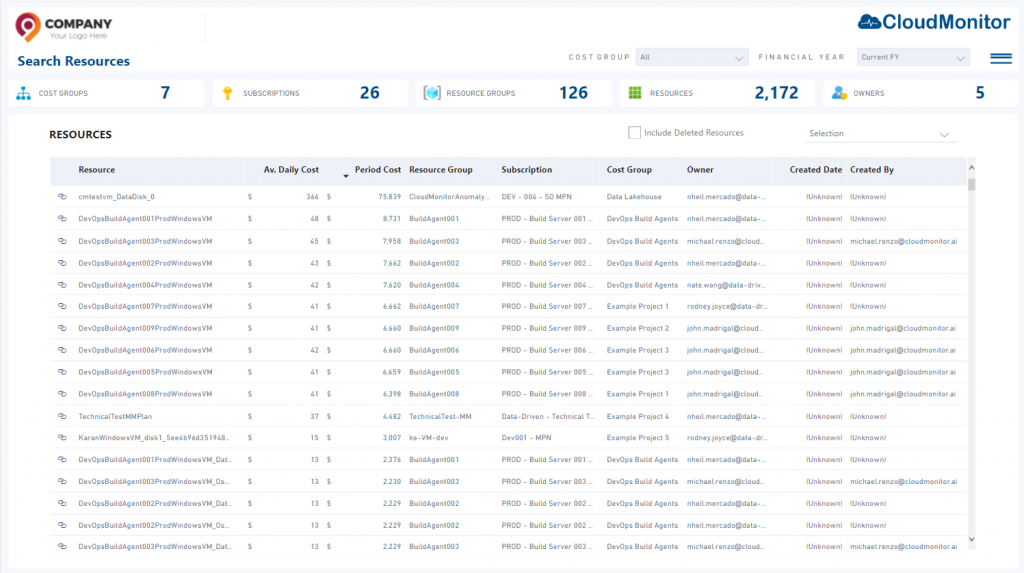
CloudMonitor provides meaningful dashboards that show top insights into your Azure environment and key metrics that align well with your business-critical goals.

Rodney Joyce
- 5 Essential Things Every FinOps Team Needs - July 23, 2024
- 5 Best FinOps Principles and How to Apply Them in a Software Development Circle - July 16, 2024
- Automating FinOps: Tips and Best Practices - July 9, 2024