Information Trust Center
CloudMonitor leverages the security features of the Azure cloud to ensure your data is secure, protected and safe. In addition, your data does not leave your cloud tenancy, which means that it stays within your organization.
Keeping client data secure is our top priority.
We value your trust and have implemented an extensive system of security controls and practices to ensure that your information and data are secure.
Your data never leaves your system.
Our CloudMonitor IP leverages the Azure Managed Application deployment model to ensure that all data and analytics remain inside of your tenancy. We do not extract your data into our SaaS application – it lives inside of your cloud and never leaves.
CloudMonitor cannot read the data in your services – only cost and meta data about services
For example, the Service Principal cannot read secrets in key vaults, data and schema objects in SQL Databases or data on Storage Accounts (or any other Azure Service). It only reads cost and metadata about these services.
CloudMonitor cannot update anything in your Azure estate
You create the Service Principal that has Read-only access and you choose which Subscriptions to monitor in CloudMonitor. It is therefore physically impossible for CloudMonitor to make any updates to any Azure Resources.
Strict Access Control is a Must
We employ significant standard controls to ensure your data remains secure. CloudMonitor actively employs a policy of least provisioning, where employees are only granted the minimum system access to perform their assigned job functions. Active Directory and cloud-native authentication and authorization is used by default.
Our Cloud Partners are ISO27001 and SOC Compliant
CloudMonitor stores its data in Microsoft Azure data centers. All of the data centers have achieved ISO/IEC 27001 and SOC 1 certification, PCI DSS Level 1 compliance. Learn more about Microsoft Azure security measures.
Our Information Security Policy handles risk scenarios
CloudMonitor believes it is essential to investigate all potential vulnerabilities. We have clearly defined procedures to fully investigate all reported issues. Click here to read our Information Security Policy.
You can trust us to keep your data secure and confidential
Please see our Data Security Statement or send us an email at [email protected] for more information if you’d want it in more depth about our security. We are happy to go into further detail and offer more insights into our policies and practices.
All data is encrypted – At rest and in transit
All information that we receive and transmit is fully encrypted. We are committed to using the most advanced encryption techniques to ensure that you are as protected as possible. You choose in which region your data is stored.
Reliability is key to a successful service
CloudMonitor has partnered with Microsoft Azure to provide the highest level of availability by employing standard high availability and reliability best practices to ensure that CloudMonitor suffers no downtime., the
CloudMonitor installs inside of your Azure Cloud Tenancy as an Azure Managed Application. The benefit of this is that data does not leave your Tenancy.
You can read more about Azure’s deployment model for Managed Applications here.

The CloudMonitor product consists of the following components:
CloudMonitor Analytics Engine
- The Engine is installed from the Azure Marketplace.
- It is our custom IP that converts the raw cost data into useful analytics and recommendations
- This is installed in your Azure Subscription as a Managed Azure Application (See architecture above)
CloudMonitor Power BI Reports
- This is the main user interface to see cost trends and analytics
- It is installed from the Azure Marketplace as a Power BI Application and connected to the Engine.
- It uses your Azure AD to authenticate and authorize users
CloudMonitor Admin App
- This is used to create Cost Groups and remediate recommendations and cost anomalies
- It is installed as part of the Engine and hosted as a Static Web Application
- It uses your Azure AD to authenticate and authorize users
CloudMonitor Teams Bot
- Provides real-time cost anomalies and alerts as part of your workflow
- It is installed as part of the Engine and hosted as an Azure Bot Service
- It uses your Azure AD to authenticate and authorize users

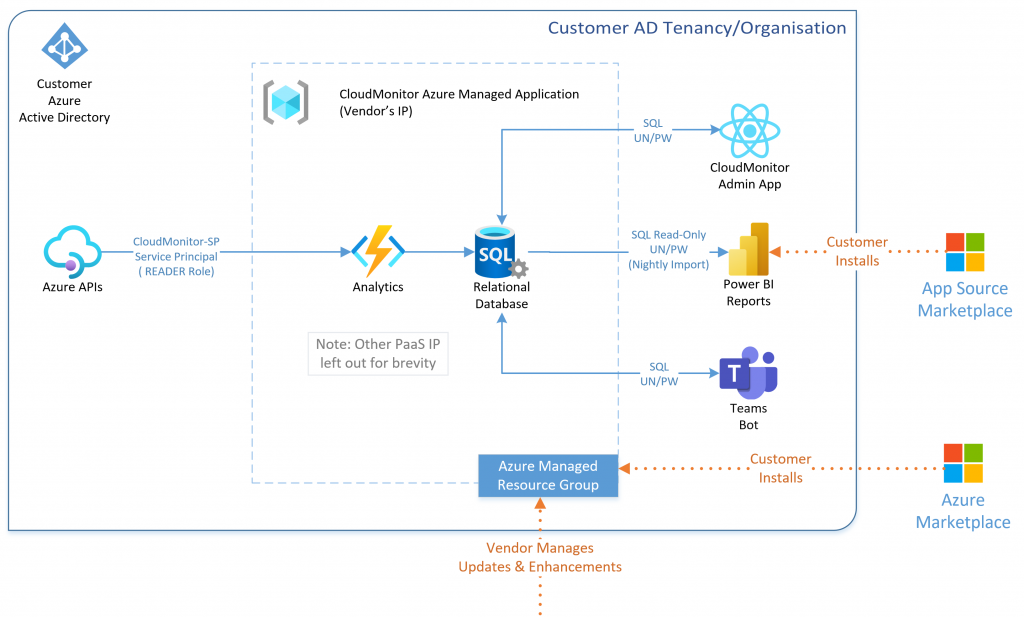
Key Points
- This Azure deployment model is the Azure Managed Application – see the benefits here.
- No data leaves the Customer’s AD Tenancy/Organisation. All analytics are processed by CloudMonitor locally.
- All data is encrypted natively by Azure at rest and in transport
- The CloudMonitor Application uses all native Azure PaaS components
- READER RBAC Role can read Azure service plane meta data and costs. It cannot read data inside of databases, key vaults, etc. at the data plane level.
- The Vendor (CloudMonitor) has Contributor access on the Managed Resource Group (which contains their IP) in order to manage the application
- Managed Resource Group Security Attestation
- PenTest – Executive Summary Report (Available on Request for Customers)
- PenTest – Detailed Summary Report (Available on Request for Customers)
- Information Security Policy
- Data Security Statement
- Modern Slavery Policy
- Azure 27001 Compliancy
- Azure SOC 1 Compliancy
Where is my data hosted?
Your raw data is stored in the Managed Resource Group in the Subscription that you choose on your Azure cloud tenancy when you install CloudMonitor (ie. it is inside of your Azure tenancy). The region of this Resource Group (which is nominated by you at install time) determines in which Azure Data Center your data will physically be stored.
We recommend that you choose the usual region closest to where your business users are to achieve the best performance.
Does my cost data ever leave my cloud tenancy or organization?
No, we are not a multi-tenanted SaaS product and therefore do not need to extract your data. All of your analytics are created inside of your cloud where CloudMonitor is installed.
This deployment model is called the Azure Managed Application.
How does the CloudMonitor Team manage the installed CloudMonitor Application?
When the Managed Resource Group is installed, a CloudMonitor Service Principal is given Owner access on the CloudMonitor IP so that we can manage the application and install updates as new versions come out. We use this Service Principal to deploy new updates via DevOps.
If the CloudMonitor Support team needs to connect to the CloudMonitor Engine to debug an issue, they will do so via Azure AD and MFA. They are unable to see any other Resource Group on your cloud estate and cannot read or change anything other than the CloudMonitor managed application.
What can you see inside of my Azure tenancy?
At a Subscription and Resource Group level, we only are able to see the Managed Resource Group containing our CloudMonitor IP. This is made up of 120+ Azure services that process your raw cost and service metadata into recommendations and useful analytics.
We do not have access to any other Resource Groups or internal systems on your cloud estate.
The Service Principal that you provide has READER RBAC access to extract costs and resource metadata (it cannot read the data inside the resources, e.g. on SQL Databases or Storage Account data) – we use these APIs to build up the Resource Graph of your system and the associated costs.
Read a 3rd-party Cyber Security Experts’ attestation on how the CloudMonitor deployment model works.
Can you read my customers’ data?
No, a Service Principal with the READER RBAC role cannot read the data inside of Azure services like key vault secrets, storage data or SQL Database data. It is physically impossible. CloudMonitor only needs access to the Cost and metadata on the Azure service plane, not the data plane.
Can the CloudMonitor Support team see my cost data?
Technically, yes, as the cost data is ingested into the CloudMonitor Managed Application (our IP that creates recommendations and analytics). Our support staff are able to theoretically read this raw data.
However, we rely on our HR Policies, user training, and information security policies to ensure that no data is ever extracted from your system and that our support team only views your cost data if absolutely necessary for support. In this case, we will ask you for permission first.
The Service Principal that you create when you install CloudMonitor provides READER IAM access on the Azure Subscriptions of your choosing, which means that the CloudMonitor application can read service-level details about your Azure Resources, as well as raw cost data, which is then converted into the Analytics shown by CloudMonitor.
As an example, the application reads the Azure SQL Database Compute and disk size (Azure Service Plane), however it would NOT be able to read any of your SQL data contained on the SQL Database (Data Plane).
We use the Service metadata such as size to create recommendations and cost anomalies.
How does Power BI, the Teams Bot and the Admin Application connect to the CloudMonitor Engine?
Currently, there are 3 CloudMonitor UIs that connect to the resources inside of the CloudMonitor Managed Resource Group: The Power BI Reports, the Admin App (Web App), and the CloudMonitor Teams Bot.
All 3 apps connect over HTTPS (public internet) to services in the Resource Group and use a SQL Username and Password to connect. These credentials are stored in the Azure KeyVault.
How do user’s authenticate with the apps?
The CloudMonitor Admin chooses who can access CloudMonitor and grants access to the Power BI reports via the standard Power BI sharing mechanism. Users log in to Power BI using standard Azure AD Authentication and Authorization is handled by your Azure Active Directory.
We recommend enabling MFA and following standard best practices for configuring Azure AD.
Is my data in CloudMonitor encrypted?
Yes, we use the standard Azure security controls to encrypt your data at rest (in Storage Accounts and SQL Databases) as well as in transit over HTTPs.
Read more about how your data is encrypted at rest here.
Read more about how Azure encrypts data in transit here
Can the CloudMonitor Support team see any data in any of my resources?
Absolutely not. The Reader RBAC role assigned at the Subscription level can only read Service Plane data, not any data inside of the resources (e.g. we cannot read data on your databases, keys in your key vaults or data on your storage accounts).
Read a 3rd-party Cyber Security Experts’ attestation on how the CloudMonitor deployment model works and what we can see.
What happens if I want to delete CloudMonitor?
You can delete CloudMonitor with a single click. All raw data and created analytics will be deleted immediately and all traces of it will be removed from your tenancy. We do not store any of your data.
Has the CloudMonitor Application been PenTested?
Yes, we do thorough pen-testing with a certified, 3rd party cyber security expert. You can see the results of the most recent pen-test here:
- Executive Summary Report (Available on Request for Customers)
- Detailed Summary Report (Available on Request for Customers)
Can we sign an NDA?
Absolutely. We can use ours or you can send us yours for additional peace of mind.
Go to our Helpdesk to see more FAQs
